- IP SLA Monitor will be configured in conjunction with the track feature to monitor the connection/reachability to the Primary ISP connection. In the event of failure, the primary default route will be removed and will failover to a backup route.
- This document also explains how to configure Network Address Translation (NAT) when there are multiple ISP's for internet connectivity and you want seamless failover i.e. When Primary ISP goes down then Secondary takes over with correct NAT with the use of the secondary ISP's public IP address.
Bigleaf’s intelligent SD-WAN features auto-detect your application needs and adapts in real-time to internet performance and connectivity issues before they impact your business. That means, unlike traditional policy-based SD-WAN solutions, Bigleaf gives you the uptime and performance you need without the complexity and risk of manual configuration.
As far as your network is concerned, Bigleaf becomes your new ISP. Your underlying Internet circuits are abstracted away, so your network doesn’t have to concern itself with changing IP addresses.
Failover is when you have one ISP set as your primary, and the second ISP is used only as a backup. When the first experiences an outage, the second ISP is there to take over everything until the primary ISP can get up and running again.

This works because before your traffic traverses the path between our gateway clusters and your building, we encapsulate each packet in a tunnel. This encapsulation enables us to provide you with static public IP addresses that don’t change when your traffic moves between ISP connections. You can use Bigleaf IP addresses, or if you have your own portable block we can route that for you. We don’t NAT or proxy your traffic, so every application works as intended.
Why does this matter? Because with Bigleaf, when one of your Internet circuits has an outage, you don’t. Your IP address doesn’t change. Your VPN, remote desktop session, SSH session, VoIP call, Web Presentation, and every other application stays up!

For maximum reliability you should use at least 2 ISP connections. The benefit of this is that you’re insulated from many issues. In addition, we recommend that you use physically diverse paths coming in to your building from unique providers, such as: fiber and cable, DSL and fixed-wireless, or T1 and cable, that way you’ll have the ultimate in Internet redundancy.
You'll Be Protected From
- Cable cuts near your building, from construction, car crashes, maintenance gone wrong, or anything else
- Routing issues on any of your Internet circuits
- Scheduled and unscheduled maintenance on any of your Internet circuits
- Peering issues or disputes that could otherwise disconnect you from parts of the Internet
- Network instability one of your provider’s networks
- Packet loss due to overloaded circuits
Every trouble-prone part of your Internet path is covered by Bigleaf redundancy, and yet we still provide you with a user-friendly single handoff to plug in to your firewall or router.
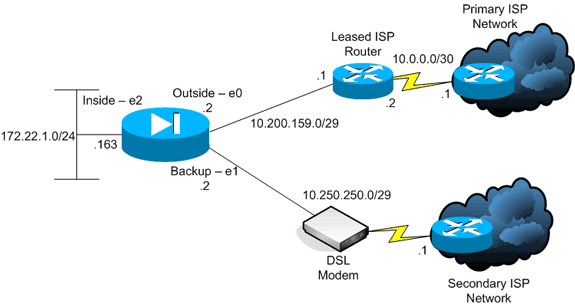
I had the opportunity to configure ISP failover on an ASA the other day and I thought I’d share the configuration as well as a couple of tips on using it. I recall that when I started working on ASA’s I would always read that ‘dual ISP’ support was a feature of the Security Plus (Sec+) licensing set. To me, that always meant that it was its own feature and had its own configuration commands. As it turns out, that’s not the case. In fact, the only reason you really need Sec+ to accomplish this is so that you have can have an additional ‘full’ interface. The rest of the configuration is really just a SLA monitor, tracked default routes, and a extra global NAT pool. Let’s walk through the configuration on a 5505. I’m going to only touch the major parts of this so please don’t consider this a full build.
Notes
-Insert your relevant information between <>
-Console prompts are show in green
-Text in blueare variable names I made up, feel free to change them
Configure your interfaces
Inside Interface
ASA(config)# interface Vlan1
ASA(config-if)#description Inside Interface
ASA(config-if)# nameif inside
ASA(config-if)# ip address <Inside IP> <Inside Mask>
Outside Interface
ASA(config)# interface Vlan2
ASA(config-if)#description Primary ISP
ASA(config-if)#nameif outside
ASA(config-if)# ip address <ISP 1 IP> <ISP 1 Mask>
Backup ISP Interface
ASA(config)# interface Vlan3
ASA(config-if)# description Backup ISP
ASA(config-if)# nameif backupisp
ASA(config-if)# security-level 0
ASA(config-if)# ip address <ISP 2 IP> <ISP 2 Mask>
Assign them to switchports
ASA(config)# interface Ethernet0/0
ASA(config-if)# switchport access vlan 2
ASA(config)# interface Ethernet0/1
ASA(config-if)# switchport access vlan 3
Notes: VLAN 1 is the default so I’m not assigning it, just use one of the other ports for it.
Configure NAT
Define your Global pools
ASA(config)# global (outside) 1 <An IP in your Primary ISPs pool that you want to use for NAT/PAT>
ASA(config)# global (backupisp) 1 <An IP in your Backup ISPs pool that you want to use for NAT/PAT>
Notes: You need to define both the primary and backup address as global pools to match up against the NAT pool. I totally forgot about that during the install and couldn’t figure out why I wasn’t passing traffic.
Isp Failover
Define your inside NAT
ASA(config)# nat (inside) 1 0.0.0.0 0.0.0.0
Notes: Some people use a specific network here, I always just use 0 0 if its a small setup
Configure the SLA Monitor
ASA(config)# sla monitor 10
ASA(config-sla-monitor)# type echo protocol ipIcmpEcho 4.2.2.2 interface outside
ASA(config-sla-monitor-echo)# num-packets 3
ASA(config-sla-monitor-echo)# timeout 1000
ASA(config-sla-monitor-echo)# frequency 3
ASA(config)# sla monitor schedule 10 life forever start-time now
Notes: Ok, so here is the actual ‘failover’ piece of all of this. So I’ll break it down piece by piece.
Line 1 – Configures a SLA monitor with the ID of 10
Line 2 – Configures the monitoring protocol and the target of the monitoring probe. In this case I chose 4.2.2.2 since I have been able to ping that magical IP address since the beginning of time. You also need to tell it which interface to source the ICMP traffic from. In this case, it would be the outside interface.
Line 3 – Sets the number of packets to be sent in each probe.
Line 4 – Configures the timeout period in milliseconds.
Line 5 – Configures the frequency of the probe in seconds.
Line 6 – Instructs the ASA to start SLA monitor 10 now and let it run for forever.
Configure the Route tracking
ASA(config)#route outside 0.0.0.0 0.0.0.0 <ISP 1 Default route> 1 track 1
ASA(config)#route backupisp 0.0.0.0 0.0.0.0 <ISP 2 Default route> 254
Notes: Here we define the default network routes out to the internet. Notice that we define out normal default route with an administrative distance of 1. However, we also add the ‘track 1’ statement at the end. This means that this route being in the routing table is dependant on tracked item 1 (If you don’t know what that means hold on, we’ll get there soon enough). We also install a second route for the backup ISP which HAS to have a higher administrative distance than the primary ISP’s default route.
ASA(config)# track 1 rtr 10 reachability
Notes: This is where the magic happens. The above statement reads like this in plain English. “Keep an eye on SLA monitor 10 and when it fails any routes associated with me also fail”. So what happens is when the SLA monitor fails, the tracked route gets removed from the routing table, and the route with the higher administrative distance comes in and takes its place since its the best available route.
Who Is My Isp
Summary
So it’s a pretty cool setup if you are ONLY looking for outbound internet failover. Keep in mind that all of your static NATs, external DNS entries, VPNs, etc won’t work when your primary ISP fails (assuming that’s the IP they are all assigned on). This particular client had me make a primary and a backup PCF file for their Cisco VPN clients so that they could access the VPN when they were in a failover state. Then I just added the backup ISP interface to the crypto map for their client VPN and turned on ISAKMP on the backup ISP interface. Keep in mind though that the backup VPN will only work when the backup ISP circuit is live and the primary VPN will only work when the primary ISP circuit is live. Both will never work at the same time.